
Top 5 Ethical Hacking Tools | Ethical Hacking Tools And Uses | Ethical Hacking | Simplilearn - YouTube
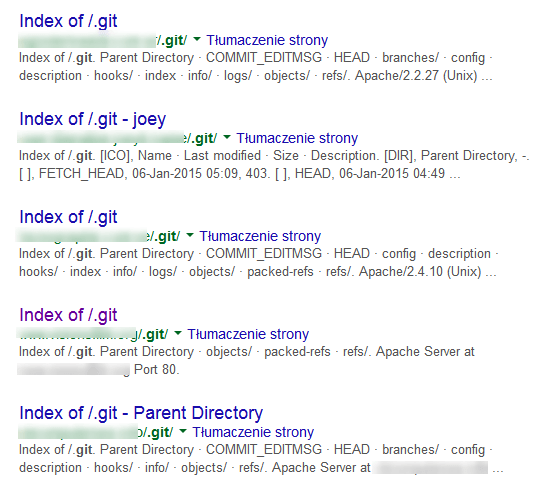
Google Hacking – How to Find Vulnerable Data Using Nothing but Google Search Engine | Objectivity Blog

Cryptocurrency Miner Uses Hacking Tool Haiduc and App Hider Xhide to Brute Force Machines and Servers - Security News



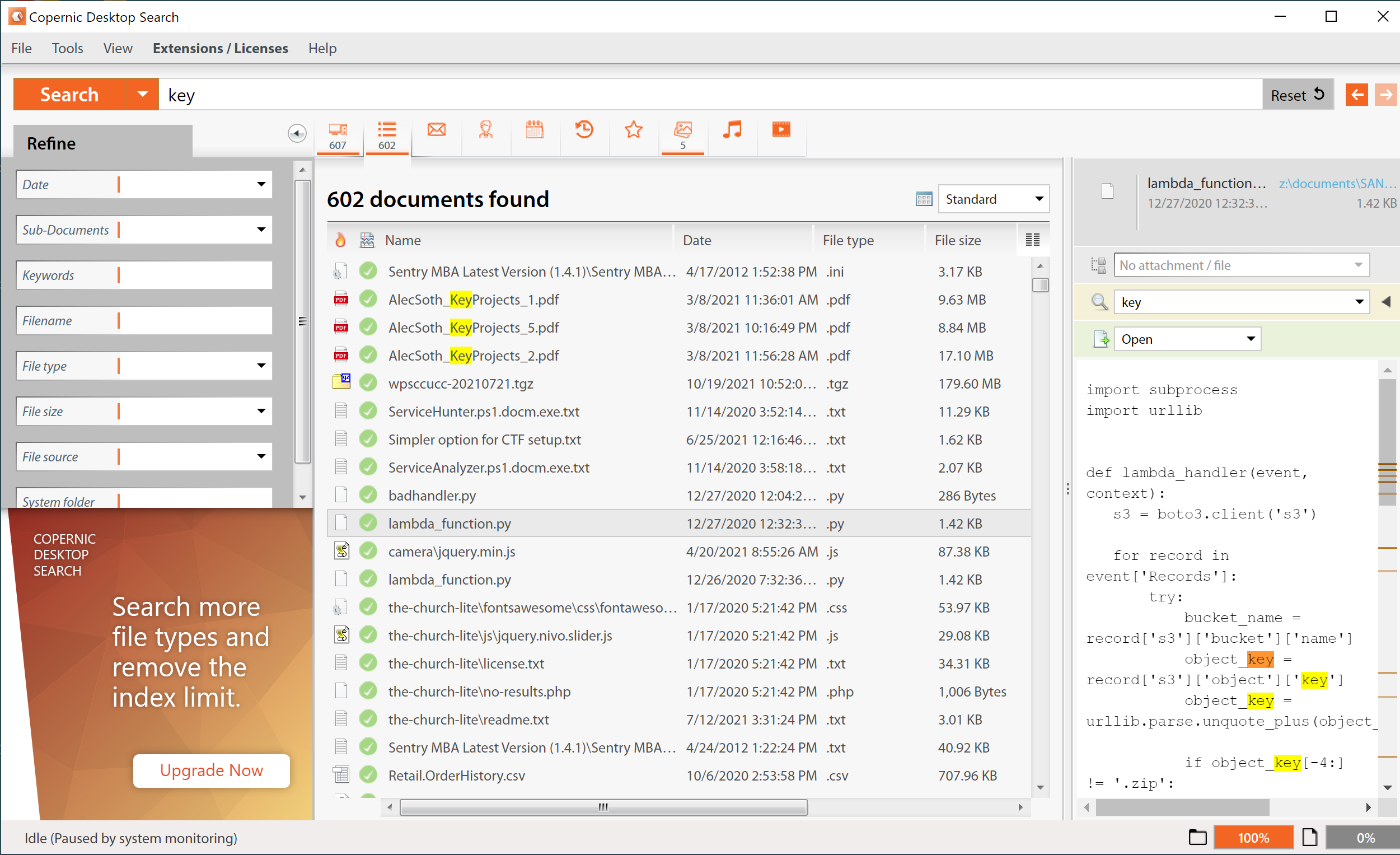









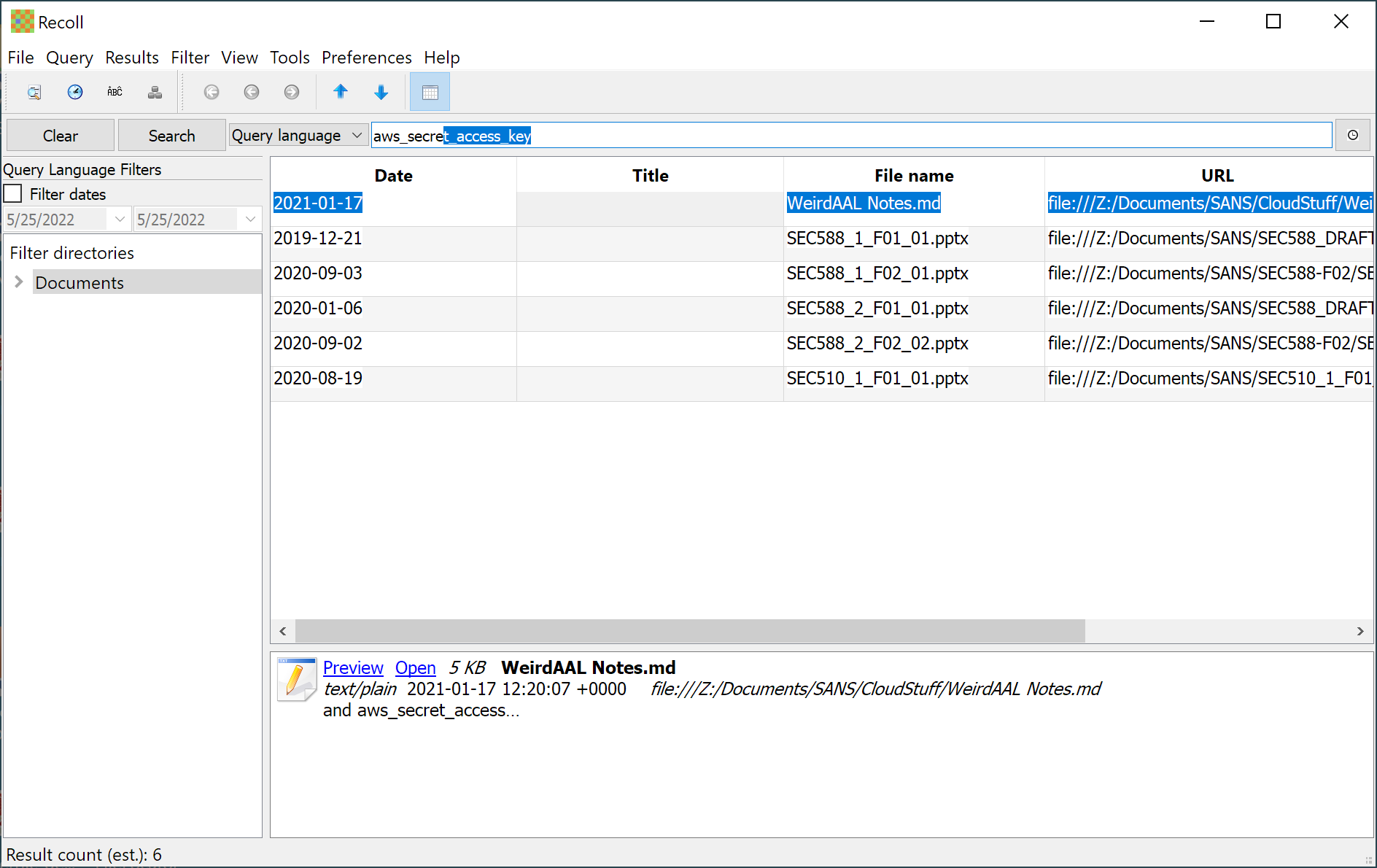



![Hacking Team [Hacked Team] Leak Unleashes Flame-Like Capabilities Into the Wild Hacking Team [Hacked Team] Leak Unleashes Flame-Like Capabilities Into the Wild](https://cdn2.hubspot.net/hubfs/3354902/Blog%20Feature%20Images/infectionscreenshot-1024x390.png)


